学习 【双语字幕】全同态加密十(几)年的发展历程】https://www.bilibili.com/video/BV1rY411V7Ko?share_source=copy_web&vd_source=4487439a1220fa77bb4a6f0079c98794
GRE
Posted on
Edited on
buffer_overflow
Assembly_language
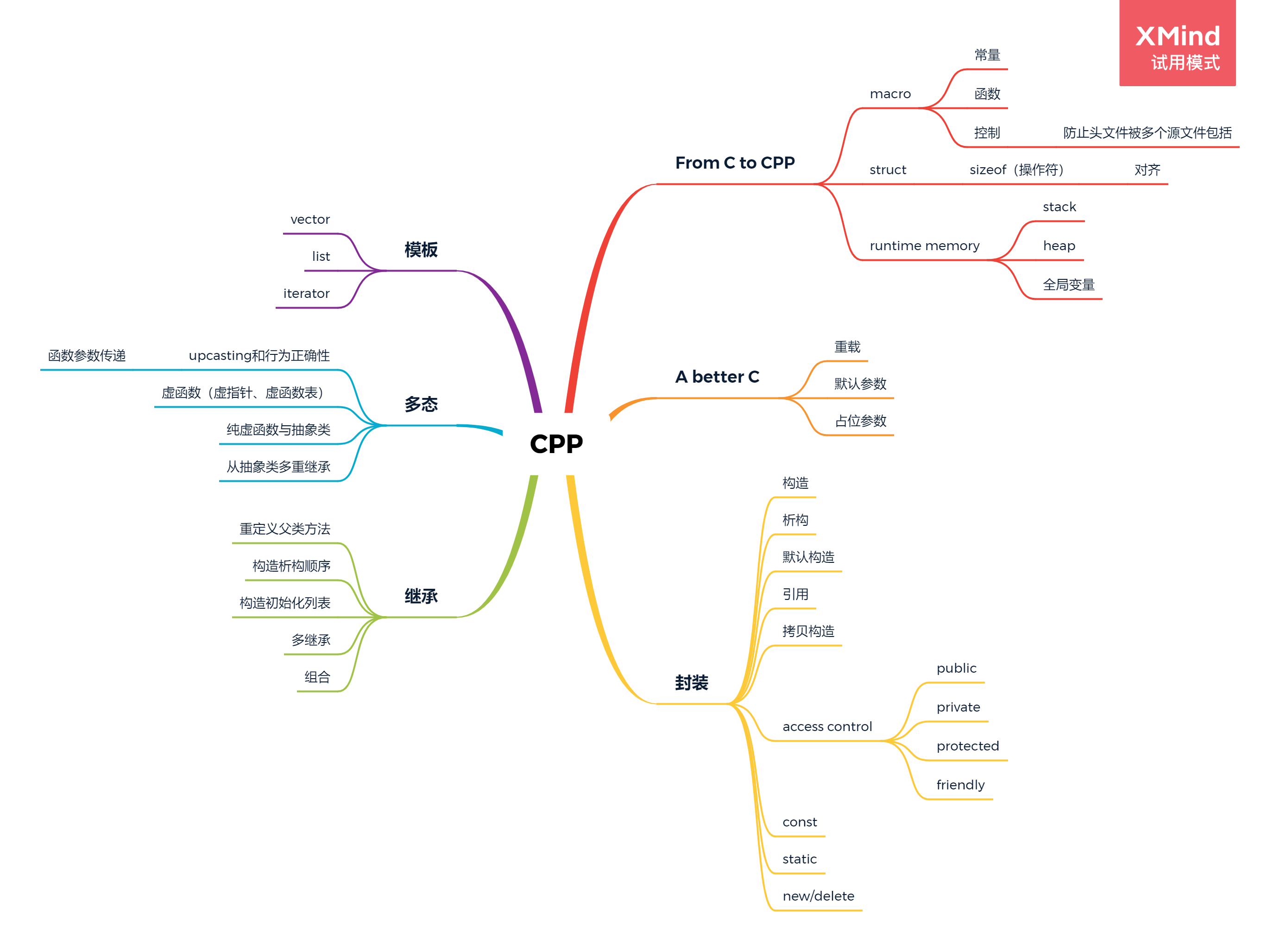
C++_OOP
Posted on
Edited on
CSAPP
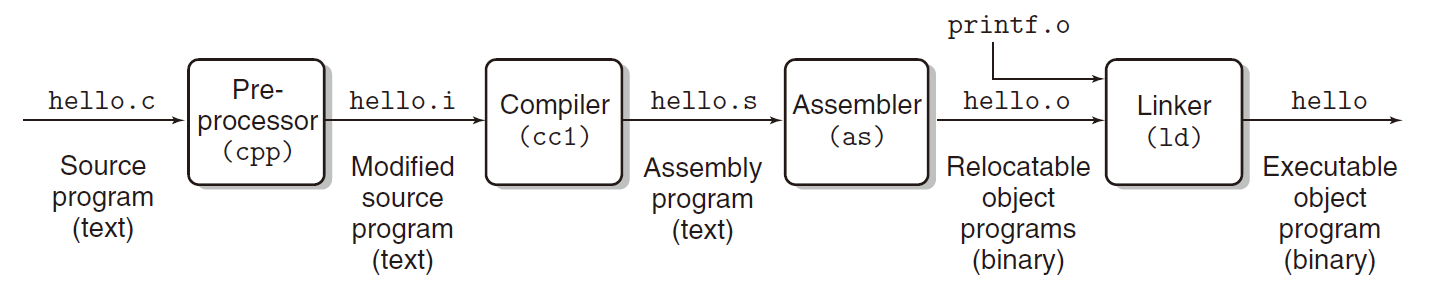
- Preprocessor: replace macro start with #
- Compiler: generates a .s file contains assembly-language program. Different compilers generate output file with assembly language.
- Assembler: translate into machine codes stored in relocatable object program
IELTS
Posted on
Edited on
“Do or do not, there is no try.”
Overall band score: 7.5 (Listening: 7.5 Reading: 9.0 Writing: 6.5 Speaking:6.5)
“End of story.”
secure protocol
virus
Posted on
Edited on